Resources
Developed by industry experts and thought leaders, IAPP resources provide the tools and information you need for your organization's AI governance, cybersecurity law and privacy programs.

New and featured resources
US State Privacy Legislation Tracker
TOOLS AND TRACKERS
Global AI Law and Policy Tracker
TOOLS AND TRACKERS
IAPP Global Legislative Predictions 2026
RESOURCE ARTICLE

Member-exclusive resources
See all reports
Organizational Digital Governance Report 2025
REPORTMEMBER

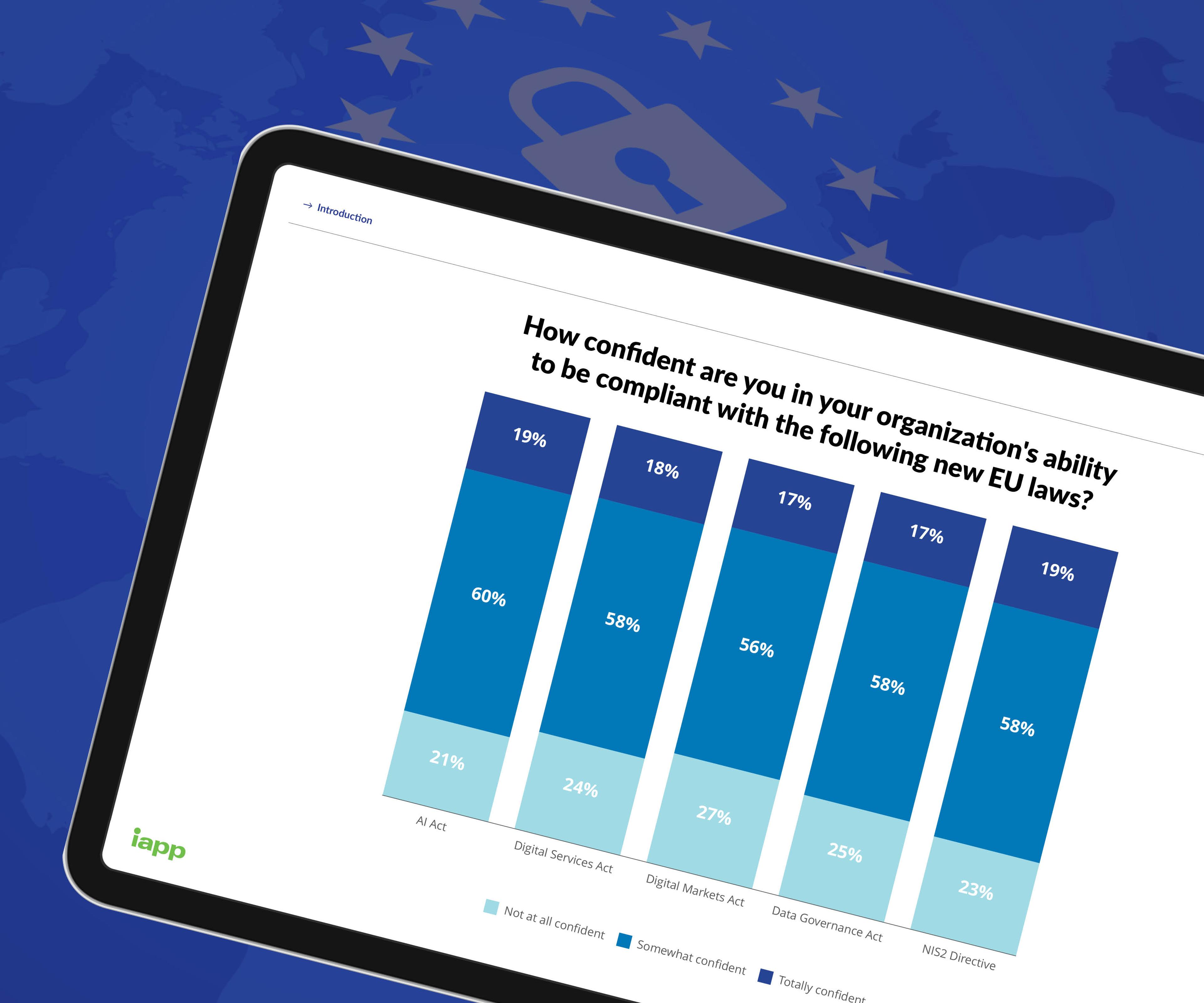
EU Digital Laws Report 2025
REPORTMEMBER
Privacy and Consumer Trust Report
REPORTMEMBER

Access member-exclusive resources
Top subjects
See all subjects
Global AI Law and Policy Tracker
TOOLS AND TRACKERS
Global AI Governance Law and Policy: Jurisdiction Overviews
RESOURCE ARTICLE

EU AI Act Regulatory Directory
TOOLS AND TRACKERS

US State Privacy Legislation Tracker
TOOLS AND TRACKERS
US State Comprehensive Privacy Laws Report 2025
REPORTMEMBER

US State AI Governance Legislation Tracker
TOOLS AND TRACKERS
California Privacy and AI Legislation Tracker
TOOLS AND TRACKERS
Head-start tools and templates
View all head-start tools and templates
Transfer Impact Assessment Templates
TOOLS AND TRACKERS

EU Standard Contractual Clauses
TOOLS AND TRACKERS

Expedited Vendor Privacy and Security Assessment Checklist
TOOLS AND TRACKERS
Consumer Privacy Notice Template
TOOLS AND TRACKERS
Data Security Program Cheat Sheet
INFOGRAPHIC

US Institutions Privacy Stakeholder Map
TOOLS AND TRACKERS

European Institutions and Regulators Digital Governance Stakeholder Map
TOOLS AND TRACKERS

Sample DPO Service Agreement
TOOLS AND TRACKERS
Sample CCPA Privacy Notices
TOOLS AND TRACKERS

Sample Data Processing Agreement
TOOLS AND TRACKERS
DPO Job Description
TOOLS AND TRACKERS
Search our library of 750+ resources
Search, filter and find the content you need — fast.
Interactive content
Web conferences, tools and trackers and other resources to take your digital responsibility program to the next level.
Live web conferences
Updates on industry trends and insights from thought leaders — right from the comfort of your own desk.
Tools and trackers
Keep up with rapid developments in digital responsibility with legislative trackers, enforcement tools and more.