This article is part of an ongoing series on privacy program metrics and benchmarking for incident response management, brought to you by Radar, Inc., a provider of purpose-built decision support software designed to guide users through a consistent, defensible process for incident management and risk assessment. Find earlier installments of this series here.
Have you noticed that every January you start seeing articles touting the previous year was the worst year on record for data breaches? It’s not just your imagination. This time last year, 2016 was cited as a “Record year for data breaches,” and 2017 has already earned the moniker “The year of the data breach,” but then again, so did 2015, 2014, and 2013. What’s more, most of these year-in-review articles warn that, while the previous year was bad, we should all brace for the year to come.
In part, these warnings ring true. If there’s something I’ve learned in my years in privacy, it’s that incidents involving private, protected information are inevitable, that concerns about these incidents will grow with each passing year and so will the volume of personal data collected and processed by entities globally. Pundits are predicting growth in the use of data through self-service IT and AI applications that I believe could further contribute to unauthorized uses and disclosures of personal data. Employee mistakes and process and system failures will continue to contribute to incident volume as in the past, along with malicious acts of insiders and external bad actors.
But how you manage these incidents, what risk mitigation factors you put in place, and whether you’ve performed a consistent and defensible multi-factor risk assessment of each incident to document your burden of proof can mean a world of difference in establishing a mature incident response compliance program and reducing risk for your 2018 incidents involving personal data.
The more things change, the more they stay the same
With this yearly warning of data breach reporting in mind, we decided to dig into our Radar metadata to do an analysis of incidents discovered in 2017. The first number we analyzed was the percentage of incidents discovered in 2017 that rose to the level of a breach, once risk assessed. We found that 19 percent of all incidents were classified as notifiable in 2017. This number is consistent with the previous year.
Next, we analyzed the percentage of incidents that were classified as notifiable within each category (paper, electronic, or verbal/visual incidents). See chart below:
2017 Incident Notification by Category
Category of Incident | % of incidents classified notifiable |
Electronic | 20% |
Paper | 19% |
Verbal/Visual | 24% |
The notification rates again remained relatively the same year over year when analyzed by incident category. This means that, for Radar users who have operationalized their incident response with technology to streamline incident intake, automate the documentation and multi-factor risk assessment of incidents, and manage notification requirements for incidents that rose to the level of notification, 2017 was no different from 2016 in terms of the volume of breaches one might expect.
Drawing from this finding and the best practices of privacy programs represented in this data set, we’ve identified a few takeaways for any organization wary of what 2018 may bring and looking to build a strong culture of compliance:
- Consistency, consistency, consistency: Customers and regulators look for a strong culture of data privacy and compliance. Using automation for documenting, risk assessing and scoring every incident is key to ensuring consistency and efficiency in the process of reporting and managing privacy incidents. Consistency is your best defense and helps avoid under or over reporting incidents.
- There is no such thing as an insignificant incident: Every incident involving personal data matters, and the presumption of breach requires every incident be consistently and defensibly risk assessed and documented in order to meet your burden of proof. See HIPAA (sec. 164.402(2)(1), GDPR - Article 33(5), and GLBA Interagency Guidance on Response Programs for just three example regulations. By assessing and documenting every paper, electronic, and verbal/visual incident without fail, you are able to demonstrate a culture of compliance and reduce organizational risks.
- Reporting and real-time dashboards allow for continuous analysis of an organization’s risk posture: You can’t see trends if you aren’t tracking the data points. Establishing objective benchmarks within your organization and analyzing your privacy program in real-time and on a regular basis is one way of identifying emerging incident trends and mitigating the underlying risk factors, before it leads to a breach.
Paper, electronic, verbal or visual: When it comes to incidents, category matters
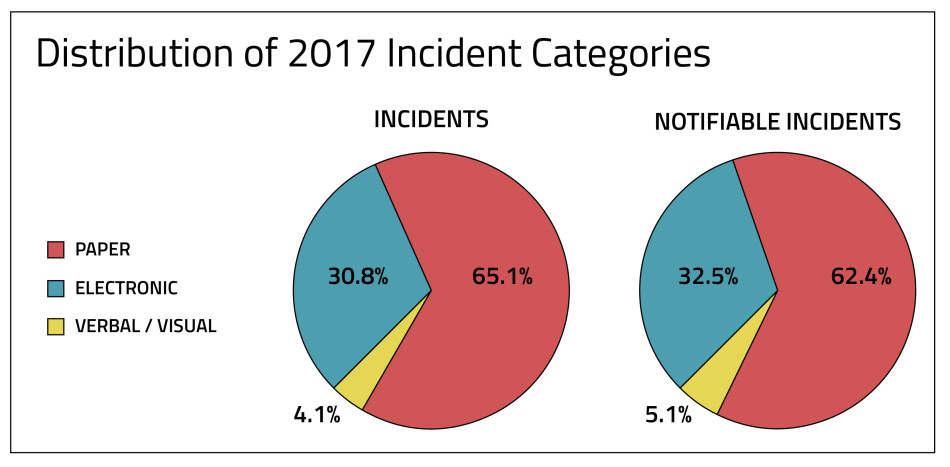
When looking at the overall number of incidents, the distribution of incidents that are paper, electronic, or verbal/visual remained more or less consistent year over year as well. Despite the fact that the treatment of paper incidents vary among states and federal breach laws, as the pie charts indicate below, the majority of incidents and notifiable incidents are paper. Paper continues to play a bigger role than commonly perceived in business interactions with customers. Electronic incidents account for about one third of incidents and also about one third of notifiable incidents. The rate at which incidents in each category rise to the level of notification remains for the most part consistent, as well.
We divided our analysis into category by form of data — paper, electronic, or verbal/visual incidents — because historically there is a tendency in the media and by some state regulators to overlook non-electronic incidents. This would be an oversight for a few reasons:
- There is a common misconception that electronic data is most at risk, when in reality electronic incidents may expose more records per incident, but paper incidents (such as misdirected mail, stolen or lost files) are still much more commonplace.
- Under the GDPR, personal data in any form is a personal data breach potentially requiring notification.
- In the U.S., there is a trend (11 states and counting) towards amending state data breach notification laws to include the regulation of paper incidents. Incidentally, if you’re a member of IAPP, you have access to free, up-to-date overviews of state, federal, and international breach notification regulations, including forms of regulated personal information, through the IAPP-RADAR Incident Response Center.
As shown in the pie charts above, the majority of privacy incidents and notifiable incidents are still paper based. You cannot afford to ignore this significant volume of incidents.
Approaching 2018: Once more, unto the breach
As we face another year of complicated compliance (and another round of hyperbolic articles about what is to come) I share a sentiment that should resonate in the heart of every privacy professional: hope for the best and prepare for the worst.
We should all prepare for 2018 to be another year in which private data gets disclosed to unauthorized parties, data breaches are reported to regulators as well as the general public, and the complexity of remaining compliant with data breach notification laws will continue to grow — especially as we see the EU GDPR go into effect in May.
That isn’t to say the future is bleak for privacy professionals. According to the hype, we’ve already experienced many “years of the data breach,” and are well-equipped to survive this coming year as well. How? To start, put your privacy program to work for 2018 and beyond. Establish program performance indicators. Ensure processes are in place to efficiently and consistently manage the incidents coming your way. Find objective ways to report on the hard work of your team in the year to come.
What’s to come in 2018? To paraphrase Shakespeare: once more unto the data breach, dear friends.
About the data used in this series: Radar ensures that the incident metadata we analyze is in compliance with the Radar privacy statement, terms of use and customer agreements. The information extracted from the platform for purposes of statistical analysis is not identifiable to any customer or data subject.

