The entire five-part series, the “Top 5 Operational Impacts of China’s PIPL,” is available in the IAPP Resource Center.
China’s Personal Information Protection Law, which is still in the process of being fleshed out through implementing regulations and official guidance, provides a regulatory framework that governs the cross-border transfer of personal information. This article focuses on PIPL and the transfer mechanisms it proposes to safeguard personal information transferred out of China.
Note that the PIPL is only one piece in the patchwork of Chinese legislation that addresses cross-border data transfers, as explained in our previous article. While the PIPL governs the transfer of personal information, China’s Cybersecurity Law and Data Security Law regulate the cross-border transfer of so-called important data, a concept which itself continues to evolve and develop through regulatory guidance. While this is not a topic that will be addressed in this piece, we note that it could be of significance to many companies operating in China.
Scope of the PIPL cross-border data transfer rules
The PIPL applies to personal information, which refers to electronic (or otherwise recorded) information related to identified or identifiable natural persons, excluding anonymized information.
The PIPL uses the term personal information processing entity to refer to an “organization or individual that independently determines the purposes and means for processing of personal information” (Article 73). This appears to be the Chinese law equivalent of the data controller concept under the EU General Data Protection Regulation.
In general, a processing entity that plans to transfer personal information to entities outside China is required to (i) provide individuals with certain specific information about the transfers and obtain separate consent (Article 39), (ii) adopt necessary measures to ensure that the overseas recipients can provide the same level of protection as required under the PIPL (Article 38) and (iii) carry out a personal information protection impact assessment (Article 55).
Note that even Article 39 explicitly requires companies to obtain separate consent for the purpose of a cross-border data transfer and that the text itself does not spell out any exceptions. Furthermore, it is unclear whether separate consent would still be required when consent was not the legal basis for processing at the point of collection. For example, it might be impractical for companies to obtain separate consent from data subjects if a company processes publicly available information relying on Article 13.6, which does not require consent at the point of collection. Further regulatory guidance might be offered on this point at a later stage.
On top of the generally applicable requirements distilled above, Article 38 offers three transfer mechanisms for companies wishing to transfer personal information outside of China. We explain these three transfer mechanisms below.
How transfer mechanisms work under the PIPL
The three transfer mechanisms offered by PIPL include security assessment, standard contractual clauses and certification. The applicability of these mechanisms depends on the characteristics of the operators.
Critical information infrastructure operators and others processing a “large volume” of personal information will need to undergo a security assessment administered by the Cyberspace Administration of China if they wish to transfer personal information outside China. The proposed process for the security assessment is described in the draft Measures for the Security Assessment of Cross-border Data Transfer, discussed below.
Non-CIIOs that do not meet the thresholds as set out in these Draft Measures do not need to go through a security assessment, but must choose one of the following lawful transfer mechanisms:
- Obtaining personal information protection certification issued by professional institutions in accordance with rules specified by the CAC.
- Entering into agreement based on SCCs stipulated by the CAC with the data recipient outside China.
Article 38 did provide a “catch all” provision that predicates a transfer on the satisfaction of other conditions stipulated by laws and regulations, but there is no information about what those other conditions might be at this point.
1. Security assessment
The first transfer mechanism detailed in the PIPL is security assessment. On Oct. 29, 2021, the CAC released the Draft Measures for public comment. Note that the CSL, DSL and PIPL all require companies to meet certain conditions to undergo a security assessment but do not provide further details. Therefore, the Draft Measures were released to further implement the security assessment requirements under all three fundamental laws.
In this section, we explain which entities are subject to a security assessment, how a security assessment works, what is assessed and what remains uncertain.
Who is subject to a security assessment under the PIPL?
The first group of entities subject to the security assessment are CIIOs. Article 40 provides that CIIOs store within China any “citizens’ personal information and important data” collected or generated in the course of operations within the country. If international transfers of data are necessary for operational reasons, a security assessment must be conducted by designated agencies unless otherwise specified by law. Any cross-border transfer of personal information by CIIOs will be subject to a security assessment.
Under Article 4 of the Draft Measures, other than CIIOs, a Chinese processing entity needs to apply to the CAC for a security assessment if it either:
- Processes personal information of over one million individuals.
- Has cumulatively transferred personal information of more than 100,000 individuals or has cumulatively transferred sensitive personal information of more than 10,000 individuals.
“Sensitive personal information” is defined under the PIPL as “personal information that, once leaked, or illegally used, may easily infringe the dignity of a natural person or cause harm to personal safety and property security, such as biometric identification information, religious beliefs, specially-designated status, medical health information, financial accounts, information on individuals’ whereabouts, as well as personal information of minors under the age of 14” (Article 28).
Note that a processing entity that transfers important data out of China is also subject to the security assessment requirement.
How does a security assessment work?
Article 6 of the Draft Measures requires data processing entities to submit the following materials when applying for the security assessment for cross-border data transfer:
- Application form.
- Self-assessment report.
- The agreement to be entered into between the data processing entity and the overseas recipient or other legally binding documents.
- Other materials required for the security assessment.
The high-level workflow of the security assessment process is summarized in the chart below.
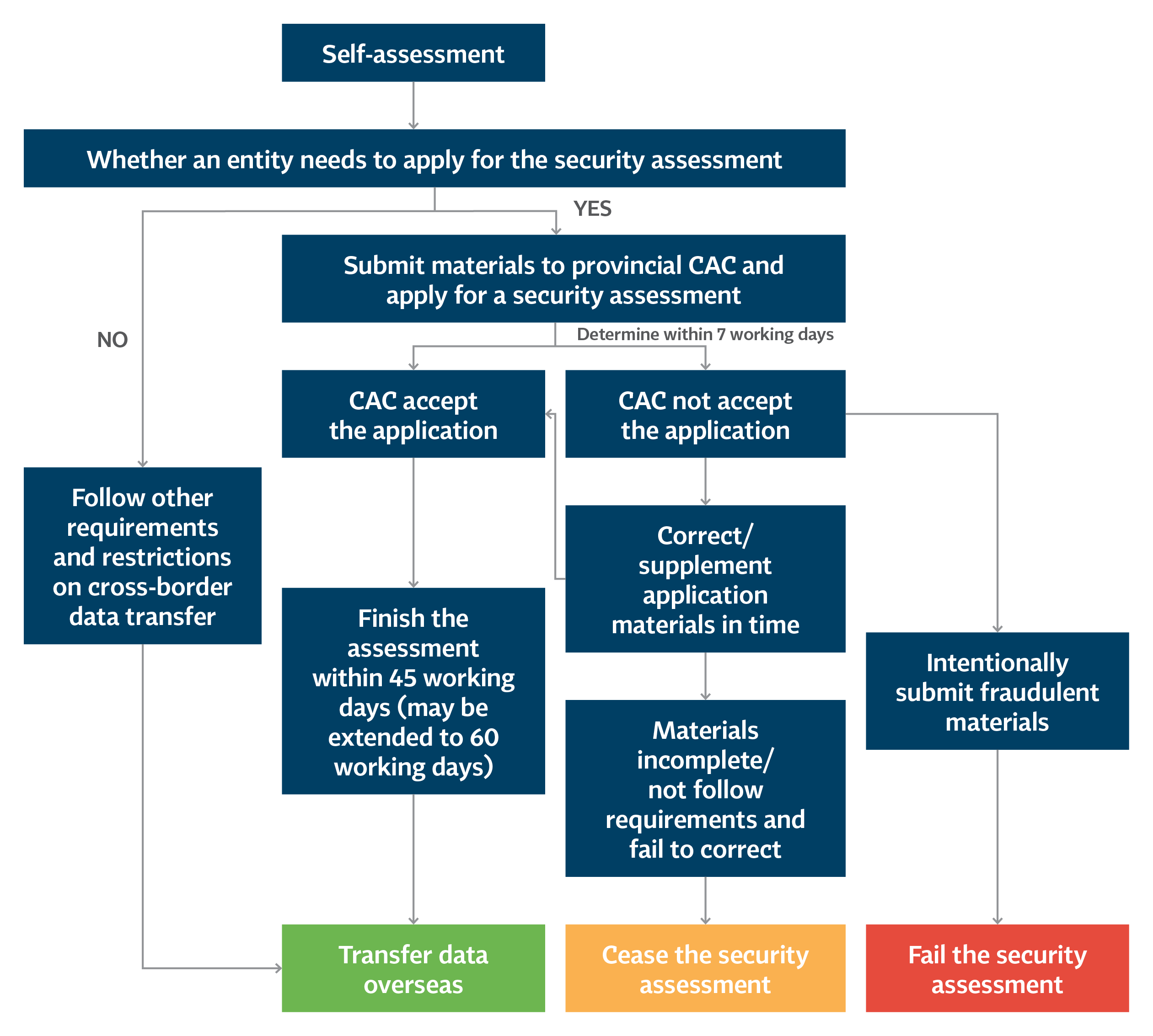
So far, the CAC has not released the template application form or any template self-assessment report.
What is the security assessment assessing?
Article 8 of the Draft Measures lays out the following criteria the security assessment focuses on, including: the legitimacy and necessity of the purpose and method of the cross-border transfer; the level of protection offered to the transferred data under local laws and the recipient’s policies; the amount, type and sensitivity of the data, as well as risks of leakage, loss or illegal access during and after the transfer; and the adequacy of the agreement between the data processing entity and oversea data recipient.
What we still do not know about the security assessment
There remain several key uncertainties regarding the security assessments even after the release of the Draft Measures. For example, the Draft Measures are silent on the length of time for calculating cumulative transfers. Further, for group companies with multiple subsidiaries and affiliates, it is unclear whether the calculation of the number of individuals whose personal information has been processed or transferred overseas shall be conducted by each subsidiary and affiliate separately or by the group company altogether. While we had expected a final version of the Draft Measures to have been released—the current Draft Measures have not been updated since December 2021—such an update has not yet been published.
Finally, although outside the scope of this article, we also note that the Draft Measures focus on the security assessment for cross-border data transfers and do not provide specific rules on the data localization requirements. In other words, the Draft Measures do not clarify whether data localization is a pre-condition to cross-border data transfer for companies that might at the same time be subject to the data localization requirements. It is also unclear whether companies that are subject to the security assessment requirements would have a heightened risk in terms of having the data localization requirements applied to them.
2. Standard contractual clauses
As of today’s date, the CAC has not yet released further guidance on the two other transfer mechanisms. In particular, there have been no template or standard contracts published by the CAC that would allow parties to satisfy the requirements of Article 38.3 of the PIPL.
However, the Draft Measures do give some guidance on what the CAC may expect to see in such transfer contracts. For reference, Article 9 of the Draft Measures indicates that the security assessment will include an evaluation of whether the contract between the data processing entity and the overseas recipient “fully stipulate(s) the responsibilities and obligations of data security protection,” which the CAC explains shall include:
- The purpose, method and scope of transferred data, and the use and method of data processing by the overseas recipient.
- The overseas location that will retain the transferred data and the retention period of such data, as well as the measures to be taken when the retention period is reached, the agreed purpose has been achieved or the contract is terminated.
- Provisions that restrict the overseas recipient from re-transferring the data to other organizations and individuals.
- Security measures to be taken by the overseas recipient in the event of a material change in its actual control or business scope, or a change of the legal environment of the country or region where the recipient is located, which makes it difficult to safeguard the data security.
- Liability for breach of the obligations of data security protection as well as binding and enforceable dispute resolution provisions.
- In the event of risks such as data leakage, properly implementing emergency response measures and ensuring convenient means are available for individuals to safeguard their personal information rights and interests.
Even in light of the above, the lack of guidance regarding the standard contractual clauses creates considerable uncertainties as we expect many companies will need to rely on standard contractual clauses for most of their international transfers.
Expected timeline
Late last year, the CAC publicly stated it is working on the draft standard contracts, although no indication has been given when such drafts will be released for public comment.
Inferring from the standard Chinese regulatory rule-making process, once the draft SCCs are released, it is likely there will be a public comment period of one month. After that, it will likely take regulators an additional period of several months to finalize the rules, although it is difficult to predict when the final rules will take effect.
3. Certification
Lastly, Article 38.3 of the PIPL states that when personal information processing entities need to transfer personal data outside of China, the final transfer mechanism is to obtain a “personal information protection certification” offered by “professional institutions” in accordance with CAC rules. As with the standard contractual clauses, the CAC is working on guidance on the process of obtaining a personal information protection certification, but no guidance has yet been released. This is also no indication when the certification rules might be published.
We will continue to monitor these developments and encourage businesses that may be transferring personal information outside of China to do the same.
Photo by Liam Read on Unsplash