Data indicates human error prevailing cause of breaches, incidents


Contributors:
Mahmood Sher-Jan
CEO
RadarFirst
This article is part of an ongoing series on privacy program metrics and benchmarking for incident response management, brought to you by Radar, Inc., a provider of purpose-built decision support software designed to guide users through a consistent, defensible process for incident management and risk assessment. Find earlier installments of this series here.
Ransomware. Malware. Phishing. Given the types of high-profile cyberthreats that carry the most coverage in the news, there is a tendency to assume incidents exposing sensitive, regulated data occur as a result of an organization being “under attack.” Seasoned privacy professionals, however, know that in reality, the majority of incidents are inadvertent and unintentional, and can be classified as human error. And these incidents still trigger the same regulatory obligations as intentional and malicious incidents.
One notable recent example: the Equifax data breach of 2017, which exposed records of nearly 146 million Americans, was reportedly due to the mistake of employees failing to follow security warnings and code reviews in implementing the software fixes that would have prevented the breach.
Commonly quoted reports, including the Cost of a Data Breach Study from Ponemon and the annual Verizon Data Breach Investigations Report, will cite causes such as employee negligence, error, etcetera. But these studies only take into account a portion of the picture. In the case of the Ponemon study, only data breaches were included in the analysis, not incidents that didn’t require notification once a proper, multi-factor risk assessment had been performed. And in the case of the Verizon report, this report does not include an analysis with paper incidents — and remember, paper incidents make up the majority of incidents.
With this in mind, we decided to look at the anonymized Radar metadata that affords a view into both incidents and data breaches and encompasses paper, electronic, and verbal or visual disclosures to learn the nature of a typical disclosure.
Intentional, malicious, unintentional, inadvertent: What's the difference when it comes to disclosing?
Before digging into the figures available from Radar metadata, it’s important to define a few key terms we will be using. When we discuss the nature of an incident, we use three categories: intentional, malicious; intentional, not malicious; and unintentional or inadvertent. Here’s a breakdown of what each category means:
- Intentional, malicious: Incident resulting from malicious actions, such as theft, a computer virus, or unauthorized access, where the intent is to cause harm.
- Intentional, not malicious: Incident resulting from non-malicious actions, such as disclosure, unauthorized access, or employee snooping, where the intent was not to use the information to cause harm.
- Unintentional or inadvertent: Incident resulting from inadvertent actions, such as misdirected faxes, accidental emails, unintentional posting or mailing of statements, or unintentional mailing of billing records to the wrong recipient.
Properly categorizing an incident with one of the above factors into a well-developed risk assessment, weighing the severity of the incident against the sensitivity of the data exposed to evaluate the potential risk of harm to individuals.
What are the most common causes of unauthorized exposure of regulated data?
Radar metadata from 2016 and 2017 indicates that, for both incidents and confirmed data breaches, the vast majority is unintentional or inadvertent in nature. Ninety-two percent of all incidents are, and 84 percent of all data breaches were unintentional or inadvertent in nature.
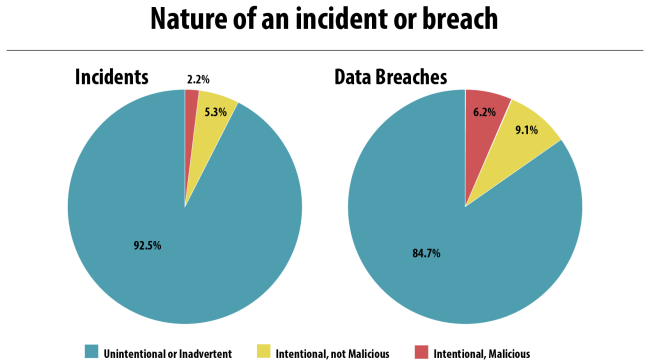
Given how relatively infrequent it is to have an incident that is intentional and malicious in nature, we decided to dig further into the data to learn the breach rate for each category. How often is an incident with a specific nature considered to escalate to the level of a data breach and thus require notification to regulators and affected individuals?
The information above also indicates that, though less common than other incidents, intentional, malicious incidents are three times more likely to be categorized as a data breach than unintentional or inadvertent incidents after performing a compliant multifactor risk assessment.
Takeaways: Intent of a data breach and improving privacy programs
We’ve said it before, and we will say it again: The fact that the majority of incidents aren’t notifiable by law does not mean that incidents do not need to be investigated, documented, and run through a multifactor risk assessment. The same goes for the nature of an incident: While the majority of incidents are inadvertent in nature, each incident still requires the performance of a multifactor incident risk assessment and breach determination, especially when upon completion of the incident risk assessment, a decision is made that the incident is not reportable. The burden of proof is on the organization to justify its decision, as well as document and demonstrate a consistent risk assessment that provides the required proof.
How can a privacy professional face these challenges head on? By building streamlined privacy processes to more consistently and efficiently manage all incidents, regardless of whether they are intentional, malicious, inadvertent or unintentional in nature. The data presented here shows that process breakdowns and poor employee training are commonplace, and the human element of our businesses isn’t going away. So build your program to reduce but account for human error. Help mitigate the impacts of human error with forward-thinking preparations. Every organization’s risk profile must account for both the possibility of attacks and the occasional mishaps due to human error. Button up security controls, implement regular training programs, and monitor the source and volume of reported incidents to keep track of trends and identify areas, be they departments, systems, or processes and controls, that could use improvement.
And never forget: Each organization must show proof of a compliant multifactor risk assessment for each non-notifiable incident and is a best practice to thoroughly document your decision process for every notifiable incident, as well. It is often only in investigating and assessing each incident that appropriate risk mitigating factors that might preclude notifications are found and exercised thus preventing over notification.
About the data used in this series: Privacy is important to us, and we take every measure to protect the data of our customers and of individuals. Radar ensures that the incident metadata we analyze is in compliance with the Radar privacy statement, terms of use, and customer agreements. The information extracted from the platform for purposes of statistical analysis is not identifiable to any customer or data subject.
Contributors:
Mahmood Sher-Jan
CEO
RadarFirst



