Health fitness app Runkeeper may be in hot water with allegations it tracked users when the app was not in use. According to Runkeeper, the issue may have been a bug in the app’s code, and there's a good chance they had no intention of tracking users outside of the app's use. That said, this is yet another case of an app surprising its users with the type of data it collects.
Of course, apps are not just privacy risks to individuals. With a rise in bring-your-own-device policies, apps pose risks for enterprises, too. It's a headache for privacy and IT pros alike.
Knowing what kinds of data apps collect, with whom they share that data, and the security with which that data is protected, is a difficult task, especially for non-technologists. Besides, who has time to match up every app’s privacy policy with its developer code? Heck, who knows what the code is actually executing?
As in so many other cases, technology and collaboration may provide a solution. The work of a small company in Virginia has created technology that analyzes and monitors apps so that enterprises – and regulators – can minimize risk of data leaks and breaches.
Fairfax, Virginia-based security startup Kryptowire offers a service that analyzes mobile apps to determine security vulnerabilities in third-party apps found in the Android and Apple app stores. More broadly, and in addition to these tools, Kryptowire offers anti-piracy solutions, security analytics, and mobile brand protection.
The development of the technology dates back to 2011 and was originally funded by the Defense Advanced Research Projects Agency and supported by the Department of Homeland Security. Kryptowire VP of Products Tom Karygiannis told Privacy Tech that 10 to 15 years ago the government ceased issuing RFPs for custom hardware, focusing instead on commercially available technology. For the mobile space, the military needed to find a way to build military-grade security into these commercial products.
Enter Kryptowire. It provided the military with a means to evaluate the security of the apps' code developed by non-military personnel. Karygiannis said, in the past, the military would have hired contractors to build custom code. Instead, Kryptowire's technology allows them to screen code developed by anyone around the world to ensure they're aligned with the military's standards.
And now that technology is available commercially. Kryptowire's technology looks at the app to assess its security, detect in-app advertisements, locate security vulnerabilities, analyze cryptographic functions, and demonstrate what data is shared with third parties. Organizations can then determine whether apps align with company privacy and security policies. For security, it can also assess whether malware is on the device.
At first, it was mainly used by the military and law enforcement, but Karygiannis said Kryptowire began looking in other areas – content piracy, most notably. He said they work with cable TV companies and movie studios to locate illegal video-streaming apps that serve up pirated content.
In the journalism space, there are apps that copy published content and run their own ads on top of it. Plus, there are many predatory apps that take advantage of trending topics to increase the likelihood of download. After the Affordable Care Act was passed, for instance, apps began springing up claiming to help users enroll in the services, when in reality they were harvesting personally identifiable information. Kryptowire’s technology can detect these bad actors.
Karygiannis said their technology is not privacy-invasive either and not downloaded onto users’ phones. Rather, the company downloads apps from the app stores and scans them in their lab. “We never have any personally identifiable information of users,” he stressed.
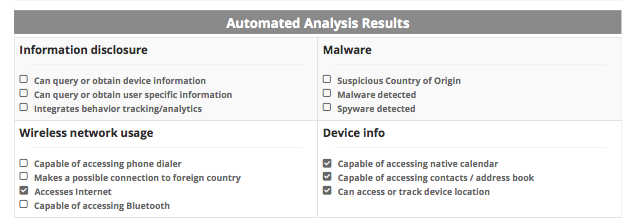
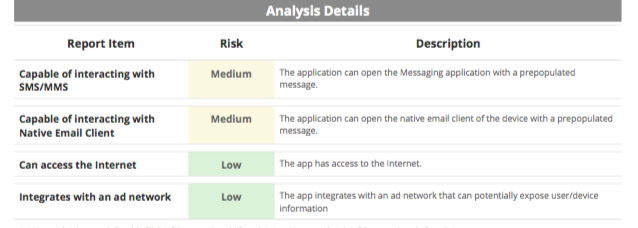
I had the chance to look at a sample analysis of an app and was impressed by its granularity and clarity. It includes basic app information, including type of encryption, and system frameworks to determine what kind of end-user data is available and whether that requires user permission. So, for example, a particular app may require permission for social media account access, but not for displaying banner-based ads in the app itself.
The report then breaks the app down into an Automated Analysis Results page and Analysis Details. The former displays as a check list for seeing information disclosure, any malware detected, file system access, among many others. The latter breaks down app details into low, medium, or high risks for the user, along with a description of why.
I first learned about Kryptowire a few weeks ago after the the enforcement arm of the Council of the Better Business Bureaus, the ARSC, took self-regulatory action against three app publishers. As a pro bono service, Kryptowire scanned apps supplied by the BBB to detect ones that were not complying with the Digital Advertising Alliance’s Self-Regulatory Code of Conduct.
Karygiannis told me Kryptowire only provided the ARSC with the technology. It was those at the ARSC who supplied the engineers with the apps for scanning. Genie Barton, who leads the efforts of the ARSC, told me that Kryptowire has been a good “adjunct to our efforts. We have a great working relationship, and we’re excited about that.”
Jon Brescia, a technology compliance specialist at the BBB, told Privacy Tech the scanning reports provided by Kryptowire were very helpful and could be tailored from granular to high-level.
He pointed out that Kryptowire’s services cover a broad spectrum, while the ARSC has deep knowledge of the advertising space: “We envision giving them feedback about what we’re experiencing when using their product and to give them the benefit of our expertise in the advertising space.”
Barton stressed the importance of collaboration and how this is a good example of self-regulators working with technology companies to find solutions. “The whole notion of collaboration," she said, "between businesses, self-regulators, academics, and regulators is an important way for us all to better understand the technologies we’re using as much as possible with the greatest granularity.”
The devices we’re all using and the apps we download may have many benefits, but the difference between what an app’s privacy policy says and what an app’s technology actually does, could be a significant one. Really, if the security of mobile apps is on your risk register, technology like Kryptowire’s might be worth looking into.
“If you have a privacy policy, and want to make sure it’s doing what it says, we have the technology that can do that,” Karygiannis said. And with millions of apps out there, and millions more to come, having technology to scan it all helps make such analysis scalable for enterprises and regulators alike.
photo credit: 09_2013_47 via photopin(license)