Unless you’ve been living under a rock for the last year, you are well aware of the California Consumer Privacy Act. This regulation first captured the attention of privacy professionals through how it came to be, originating with an unlikely champion in San Francisco real estate developer Alastair Mactaggart, gaining momentum in a post–Cambridge Analytica political climate, and speeding to Democratic Gov. Jerry Brown’s desk to receive his signature after weeks of intense negotiation between private sector privacy advocates, technology startups and government officials.
That was last September. What has kept the CCPA in the limelight in the intervening months is the scope and potential impact of the act. The CCPA is heralded by many as the most extensive consumer privacy legislation ever passed in the United States. In many ways, the CCPA is preoccupying privacy professionals in a way that is reminiscent of the EU General Data Protection Regulation about a year ago. Chief among the concerns from privacy professionals preparing for compliance with this new act are the expanded protections and rights afforded California residents when it comes to the collection of their personal information.
The new considerations in how personal information is collected, maintained and managed by organizations are compounded by how the CCPA also expands the scope of what is considered to be personal information currently outlined in California data breach laws. Taking cues from the GDPR, the CCPA’s definition of personal information broadly includes information that can identify, relate to, describe, be associated with or be reasonably linked directly or indirectly to a particular consumer or household.
Given the above and the 2020 effective date, it’s no wonder the CCPA has created considerable urgency for privacy teams in the states.
Beyond California: The influence of CCPA on changing US state privacy laws
California has long been a trendsetter in the United States. From the days of "Gidget" and beach culture to the proliferation of avocado everything, the Golden State’s influence is considerable. This is also true when it comes to privacy laws. In the months following the passage of the CCPA, several other states have made similar moves. A few standouts:
- Nevada’s Act Relating to Internet Privacy (SB 220) was passed into law in May and goes into effect Oct. 1, 2019 – three full months before the CCPA.
- The New York Privacy Act (SB S5642), introduced in May of this year, is considered broader than the CCPA as it gives residents even more control over their data and, if passed, would give New Yorkers a private right of action.
- New Jersey’s Act Concerning Commercial Internet Websites, Online Services, and Personally Identifiable Information (A-4902) was introduced right as the CCPA was passed in 2018, sharing many aspects of the CCPA but also adding notification requirements regarding the collection and disclosure of personal identifiable information to third parties.
I highlight the above to illustrate the effects of this style of rising tide regulation. The CCPA itself is said to have been greatly influenced and in part ushered into law as a reaction to the EU General Data Protection Regulation’s sweeping impacts on privacy considerations. Privacy practitioners who worked toward the GDPR’s effective date will know firsthand the dangers of a myopic approach when it comes to these headline-grabbing regulations.
You cannot lose sight of other regulatory developments while working toward compliance with a regulation like the CCPA — there are always ripples of influence when these large regulations hit the water.
Benchmarking your privacy program for CCPA: Start now
Given the accelerated pace of privacy regulation changes in the U.S. and globally, it’s more critical than ever to establish strong reporting and benchmarking within your incident response program. As new privacy laws impacting your breach notification requirements come to pass, you will need a big picture view of your organization’s privacy health, with real-time reports and dashboards to identify trends and garner insights for continual process improvements. Look to establish benchmarking metrics now so that, when new regulations go into effect, you can see the impacts on your business and the efficacy of your privacy safeguards.
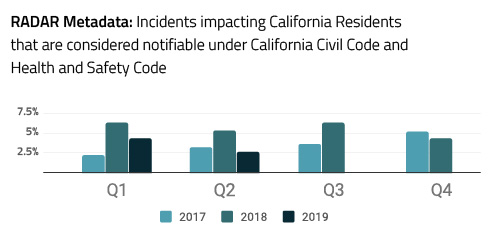
Using aggregated incident metadata available in the Radar platform, we were able to determine an overall benchmark for the percentage of incidents that are considered notifiable to affected individuals and regulators within California for the past two and a half years. When considering the following, it’s important to remember that Radar’s metadata represents organizations that exemplify organizational excellence, using incident risk assessment automation to avoid overreporting.
There is a prevailing attitude that most incidents trigger breach notification obligations in California, due to the state’s stringent breach laws and a lack of a harm standard. Contrary to this sentiment, Radar’s metadata above indicates that since January of 2017, fewer than 6% of the incidents impacting California residents were considered notifiable.
Compare this figure to the breach rate reported in 2019 BakerHostetler’s 2019 "Data Security Incident Response Report" (PDF), which notes that over a four-year period since the report was first produced, notice was provided in 53% of incidents. This discrepancy highlights a significant level of overreporting under California data breach regulations. Overreporting poses a risk to your organization’s reputation and brand — a risk you can avoid with consistent and defensible risk assessment and notification decision making.
It’s also important to note that the stats above represent the current reality under California Civil Code and Health and Safety Code for breach notification obligations. When the CCPA goes into effect, the definition of personal information will be greatly expanded, creating more opportunities for organizations without a disciplined and automated risk assessment methodology to overreport.
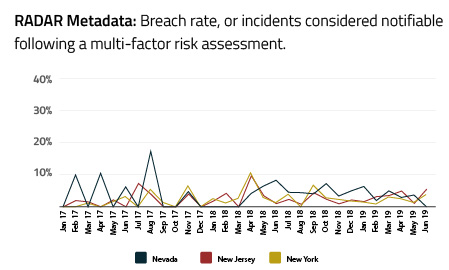
When we looked into other states with CCPA-like regulations proposed, we saw similar findings. Below are breach rates for our three example states with pending legislation earlier in the article:
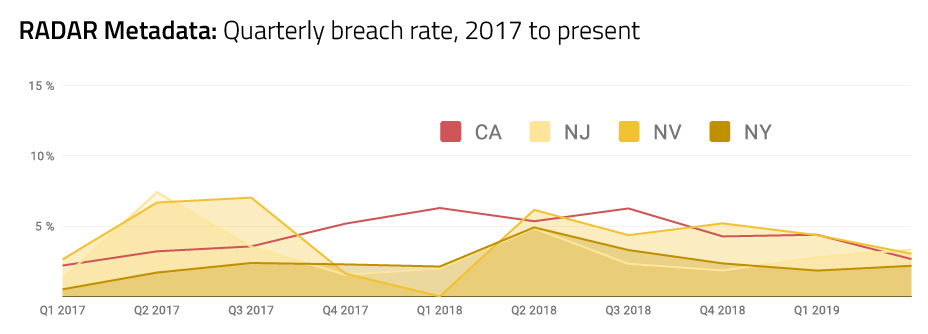
With few exceptions, the monthly breach rate (or percentage of incidents that rise to the level of a data breach requiring notification to regulators and affected individuals) in Nevada, New Jersey and New York have been relatively low. It’s also interesting to visualize this information layered together with a quarterly view.
Viewing the data this way, it’s interesting that, while California has long been a leader in setting increasingly stringent privacy laws, the results of those laws in terms of breaches reported align with other states’ breach rates to date. We aren’t seeing a lot of peaks in the chart. Generally, breach rates have remained steadily around or below 5% across the states for the last 32 months. This kind of flat line speaks to a privacy program that has achieved consistency in performing risk assessments and making a breach or no breach determination.
CCPA and lessons learned from GDPR: Beware overreporting
Over a year ago, we saw the GDPR go into effect. Now we are beginning to analyze the impacts of that regulation.
A year from now, you are going to want to be able to see the influence of the CCPA in terms of privacy outcomes. That requires you to establish strong benchmarking and reporting capabilities within your organization now with the ultimate goal of consistent, objective and defensible incident response practices.
Broadening the definition of personal information can have the effect of increasing the incident volume, time and effort required of privacy teams to perform a multifactor risk assessment to determine whether notification is required. Under the GDPR, which has a similarly broad definition of personal information, there was a notable increase in the number of breaches reported to supervisory authorities, and some regulators noted problems with overreporting. Companies that report any and everything that may be considered a data breach inevitably overreport, which highlights a lack of compliant and defensible incident risk assessment and notification decision-making.
Why benchmark?
Establishing benchmarking metrics now will help determine a baseline for comparison once CCPA (and other near-term regulations) go into effect and identify areas in the organization that require additional attention or training — areas that, if not addressed now, will only become more problematic once new regulations are underfoot.
Given that somber reality, here are a few areas to consider a more proactive approach when it comes to your CCPA preparations:
- Stay ahead of changing privacy regulations through continuous monitoring of legislative updates. Know when a regulation changes your breach notification requirements.
- Perform regular simulations and tabletop exercises to evaluate potential areas for improvement within your privacy program and most notably your incident response processes.
- Track your privacy incidents and notifications over time, making sure to capture enough detail to be able to slice the data by key metrics. Examples: number of affected individuals, jurisdiction, occurrence to discovery timeline, decision-making timeline, notification timeline, post-incident risk mitigation steps, root cause, corrective actions, etcetera. This type of data allows you to identify trends and areas for process improvement — not to mention this data provides the evidence you need to support increased budget and resources so you can ultimately better manage risk.
About the data used in this series: Information extracted from Radar for purposes of statistical analysis is aggregated metadata that is not identifiable to any customer or data subject. The incident metadata available in the Radar platform is representative of organizations that use automation best practices to help them perform a consistent and objective multifactor incident risk assessment using a methodology that incorporates incident-specific risk factors (sensitivity of the data involved and severity of the incident) to determine if the incident is a data breach requiring notification to individuals and/or regulatory bodies. Radar ensures that the incident metadata we analyze is in compliance with the Radar privacy statement, terms of use, and customer agreements.
Photo via Good Free Photos
![Default Article Featured Image_laptop-newspaper-global-article-090623[95].jpg](https://images.contentstack.io/v3/assets/bltd4dd5b2d705252bc/blt61f52659e86e1227/64ff207a8606a815d1c86182/laptop-newspaper-global-article-090623[95].jpg?width=3840&quality=75&format=pjpg&auto=webp)