Repeated headlines announcing the latest "breach" or company that was "hacked" have caused companies to believe that incidents are inevitable. Many are taking steps to be better prepared to respond when the first sign of an incident is detected—often at 4:30 p.m. on a Friday. The question then becomes, especially for companies that do not routinely face incidents, what kind of incidents should they prepare for?
The annual reports that forensic investigation firms produce are full of great information on threat vectors, industry targets and response trends. However, not every incident that affects a company requires a forensic investigation. And there are very few sources that cover the other types of incidents, e.g., lost unencrypted backup tapes, inadvertent disclosures, device theft.
This gap was one of the reasons that drove BakerHostetler’s Privacy & Data Protection Team to review statistics from more than 200 incidents we worked with clients on in 2014 and release our inaugural 2015 Security Incident Response Report, which summarizes some of the insight gained from those matters. Note—we deliberately used the term “incident” instead of “breach” because not every issue that is reported meets the definition of a “breach” under the applicable law. Ultimately, we believe our incident-response report can be used to enhance efforts by companies to become “compromise ready”—an incremental and continuous process of identifying threats, prevention and mitigation and response preparedness.
Human Error Is Frequently To Blame
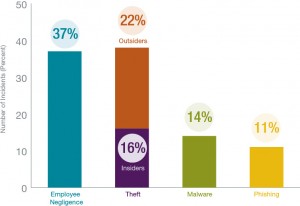
Attacks by advanced, persistent threat actors often grab the headlines, and companies are sometimes inclined to describe the incident as a sophisticated and unpreventable attack. However, similar to what the forensic investigation firms continue to report, human error is often to blame for security incidents. While phishing and spear-phishing may be the leading cause of external attacks in 2015, not every incident involves an external attack.
From our review, where a definitive underlying cause could be determined, employee negligence was the leading cause. The takeaway is that companies cannot eradicate security risk solely through the use of better technology. Building a better moat is great, but if an employee leaves the drawbridge down or is fooled by the disguise of the barbarians at the gate and gives them entry, the time and money spent implementing the new technology is wasted. While technical security solutions do help, companies must include appropriate employee training and awareness driven by the right “tone from the top” and appropriate information-security policies and procedures.
No Industry Is Immune
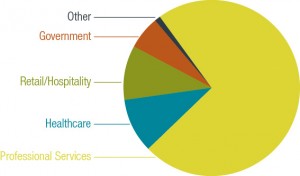
While retail and healthcare breaches garner the most publicity, it is important to note that no industry is immune.
Incidents do not only occur at businesses that have payment card data or protected health information. Industries represented in our report include education, financial services, real estate, retail/hospitality, professional services and healthcare. Not surprisingly, healthcare tops the list in frequency of incidents with professional services and retail industries topping the list for severity.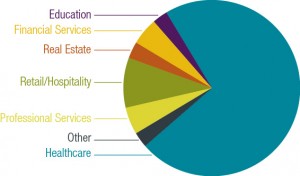
Rapid Detection Is Critical
Timing is critical at all stages of an incident response, but perhaps it is most critical at the detection and containment phase. Forensic firms report that the time from occurrence to detection exceeds six months. Because our incident mix is different—device theft and inadvertent disclosures tend to be discovered quickly—our data shows that the average amount of time between incident occurrence and detection was 134 days. There are several consequences to slow detection.
Obviously, the longer a company takes to detect and contain the incident, the more likely it is to miss an opportunity to stop the theft of sensitive data or mitigate the potential harm. In addition, forensic data that could be used to show exactly what was accessed or acquired can be lost, such as when logs are overwritten or devices restarted, often leaving the company in a position of assuming the worst-case scenario.
Last, the longer the time lapse from occurrence to detection, the more likely it is that a third party will see the signs of the incident and the incident will become public before the company itself is even made aware. Public disclosure before the company is even aware or is just beginning to investigate puts a company in a precarious situation, and intense media scrutiny at early stages of an incident has factored into companies making mistakes, e.g., saying too much in an effort to reassure and then having to update their message when the issue is worse than they initially acknowledged. Going forward we are also going to look at the time from detection to containment.
Regulatory Investigation Is More Likely than Litigation
With certain high-profile breaches, it is not uncommon for a class-action lawsuit to be filed within days of the public disclosure of an incident. If millions of payment cards or patients are affected, there is a good chance of one or more putative class-actions being filed. However, from our 2014 incidents, a regulatory investigation is far more likely than a lawsuit—31 percent of companies that gave notice of a “breach” received an inquiry or were investigated by a regulator, e.g., HHS OCR, FTC, state attorneys general, whereas only six percent of companies were eventually sued by potentially affected individuals.
Other Insights
Other key issues addressed in the report include:
- Do not forget about paper records—21 percent of the incidents we handled involved paper records and states are modifying their notification laws to cover electronic and paper records;
- How often did companies offer credit monitoring—67 percent;
- For payment card incidents, the range of the initial demand for indemnification for operating expense and counterfeit fraud to reimburse affected issuing banks was $3 to $25 per at-risk card;
- For healthcare incidents affecting more than 500 individuals, HHS OCR initiates an investigation 100% of the time.
Becoming Compromise Ready—Preparing for the Inevitable
There is no longer a debate—security incidents are inevitable. In our experience, the companies that are best-positioned to respond in a way that is viewed by their key stakeholders and regulators as handling the incident well are those that accept and plan for the inevitable through defense-in-depth, segmentation, rapid detection and containment, coupled with ongoing effort to monitor threat intelligence and adapt to changing risks, as well as testing and refining incident response plans by conducting mock-breach exercises in tabletop sessions.