How IT and Infosec Value Privacy Report
This report examines how IT and privacy teams work in concert, so that their respective spends can complement one another.
Published: 1 March 2016
As a more mature field, information security has long enjoyed larger budgets and more staff than information privacy. As privacy teams have matured and grown, however, their budgets are beginning to be substantive. How do information security and privacy teams work in concert, so that their respective spends can complement one another? Are their priorities aligned? Have firms decided that information privacy investments can enhance information security? What privacy functions are valuable in mitigating a data breach?
These are some of the questions we set out to explore in a survey commissioned jointly by IAPP and TRUSTe and fielded between December 2015 and January 2016, eliciting responses from more than 550 privacy (65 percent) and IT/infosecurity professionals (35 percent). This infographic outlines the findings of the report.
Our study confirmed the well-documented extent of the cybersecurity threat, with 39 percent of companies reporting a significant information incident in the last two years. It also confirmed that companies are increasing their infosecurity and privacy investments alike to help address this growing threat.
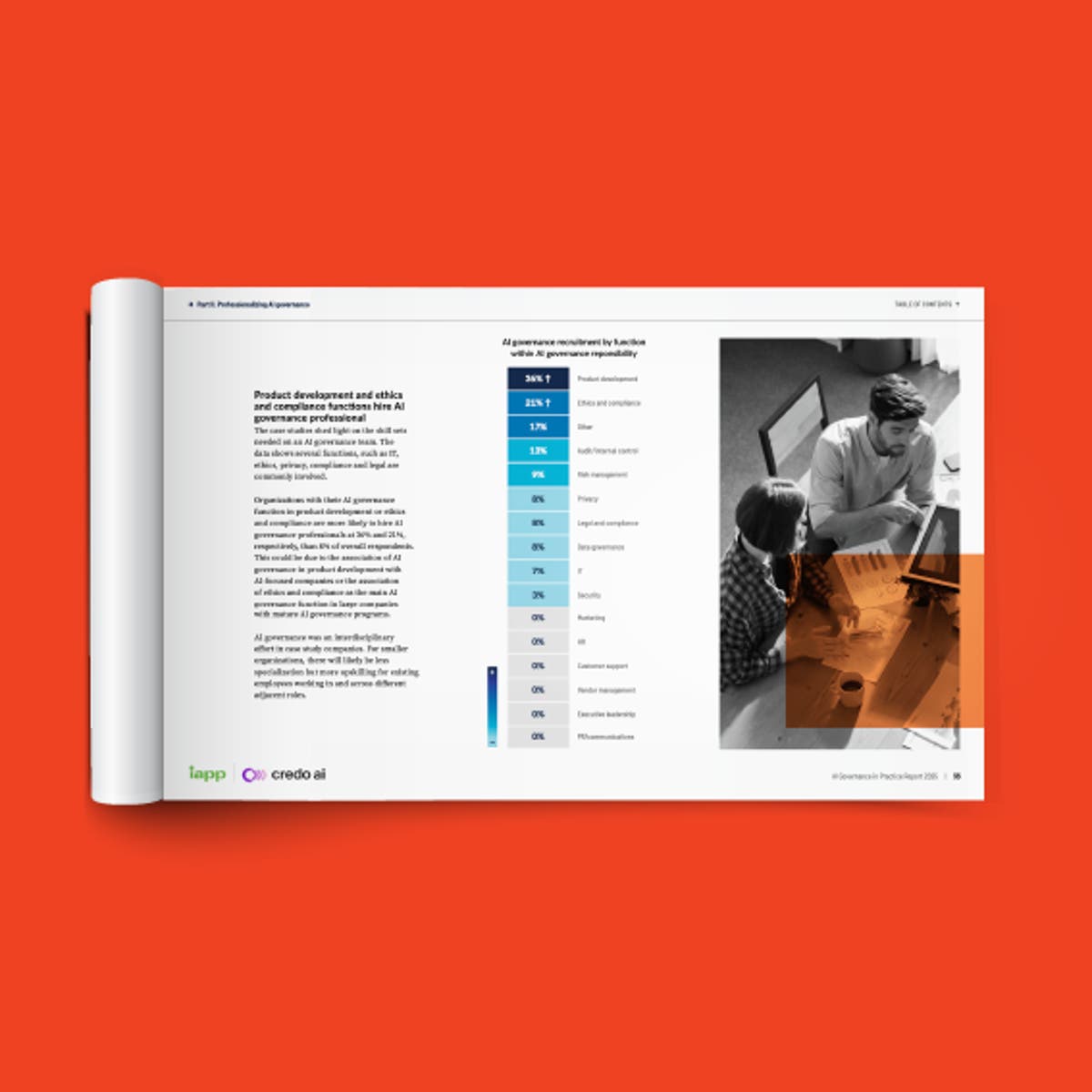
Fifty percent of companies have increased the involvement of privacy personnel on their infosecurity teams in the last two years. As they seek to get a better handle on their data and the extent of their corporate risk, they are employing core privacy functions with an IT bent: Forty-two percent increased investment in privacy technology, 41 percent reported both an increased use of privacy impact assessments and data inventory and classification, and 40 percent have increased the use of data retention policies.
In fact, privacy and security professionals alike agree that the most important feature of their information governance regime is communication between the privacy and security teams, many of which are now populated with staff from each discipline. Some 75 percent of IT/infosecurity professionals ranked data minimization and data inventory and mapping as the most important privacy functions in mitigating the risk of a data breach, followed by privacy policies and privacy impact assessments.
Interestingly, privacy technology spending is outpacing investment in personnel, as privacy growth maps that of Infosecurity over the last 10 years. The study found that 42 percent had increased their spending on privacy-related technology — well ahead of spend on external counsel (34 percent) and external auditors (26 percent).
In addition, although regulatory enforcement actions are rare, firms find privacy investments highly important after they occur. While 39 percent of respondents reported a significant cyber incident, the existence of that incident did not seem to move the budget need for privacy. However, when a regulator became involved, suddenly the budget increased and the emphasis on privacy practices became more pronounced.
Perhaps investors and boards should question why companies seem to be waiting for the regulator to call before prioritizing privacy spend.

This content is eligible for Continuing Professional Education credits. Please self-submit according to CPE policy guidelines.
How IT and Infosec Value Privacy Report
This report examines how IT and privacy teams work in concert, so that their respective spends can complement one another.
Published: 1 March 2016
As a more mature field, information security has long enjoyed larger budgets and more staff than information privacy. As privacy teams have matured and grown, however, their budgets are beginning to be substantive. How do information security and privacy teams work in concert, so that their respective spends can complement one another? Are their priorities aligned? Have firms decided that information privacy investments can enhance information security? What privacy functions are valuable in mitigating a data breach?
These are some of the questions we set out to explore in a survey commissioned jointly by IAPP and TRUSTe and fielded between December 2015 and January 2016, eliciting responses from more than 550 privacy (65 percent) and IT/infosecurity professionals (35 percent). This infographic outlines the findings of the report.
Our study confirmed the well-documented extent of the cybersecurity threat, with 39 percent of companies reporting a significant information incident in the last two years. It also confirmed that companies are increasing their infosecurity and privacy investments alike to help address this growing threat.
Fifty percent of companies have increased the involvement of privacy personnel on their infosecurity teams in the last two years. As they seek to get a better handle on their data and the extent of their corporate risk, they are employing core privacy functions with an IT bent: Forty-two percent increased investment in privacy technology, 41 percent reported both an increased use of privacy impact assessments and data inventory and classification, and 40 percent have increased the use of data retention policies.
In fact, privacy and security professionals alike agree that the most important feature of their information governance regime is communication between the privacy and security teams, many of which are now populated with staff from each discipline. Some 75 percent of IT/infosecurity professionals ranked data minimization and data inventory and mapping as the most important privacy functions in mitigating the risk of a data breach, followed by privacy policies and privacy impact assessments.
Interestingly, privacy technology spending is outpacing investment in personnel, as privacy growth maps that of Infosecurity over the last 10 years. The study found that 42 percent had increased their spending on privacy-related technology — well ahead of spend on external counsel (34 percent) and external auditors (26 percent).
In addition, although regulatory enforcement actions are rare, firms find privacy investments highly important after they occur. While 39 percent of respondents reported a significant cyber incident, the existence of that incident did not seem to move the budget need for privacy. However, when a regulator became involved, suddenly the budget increased and the emphasis on privacy practices became more pronounced.
Perhaps investors and boards should question why companies seem to be waiting for the regulator to call before prioritizing privacy spend.

This content is eligible for Continuing Professional Education credits. Please self-submit according to CPE policy guidelines.
Tags:
Related resources
US State AI Governance Legislation Tracker
US State Privacy Legislation Tracker
Global AI Law and Policy Tracker
IAPP Global Legislative Predictions 2026
