Around the office the last few months, we’ve taken to referencing a famous quote by Arthur Nielsen: “The price of light is less than the cost of darkness.”
That’s a profound sentiment. And speaks to the real cost and pain associated with working in the dark without insights. We at RadarFirst talk about this through the lens of measuring the success of your incident response program. It is often a painful process to begin — and initially can highlight results you may find risky and unacceptable. Ultimately, it’s not really a question of whether it's worth it to measure and invest in your privacy program, but rather a question of whether you can afford not to. You can’t change without a baseline and a benchmark for success.
The ROI of benchmarking your incident response program
Many privacy professionals, especially those who have been in the field for a long time and witnessed the growth of our profession, have traditionally struggled to quantify the organizational value of privacy best practices and secure budgets. Arming yourself with benchmarking statistics can give you a shorthand when explaining to your executives and management the importance of investing in incident response within the organization, especially when it comes to reducing enterprise risk, creating efficiency and protecting the brand.
There are two critical elements here: the industry statistics for drawing comparison and the operational metrics from within your organization. Both are critical for demonstrating if your organization is operating within the bounds of industry standards when it comes to incident response. Are you doing enough? Are you lagging behind? How do you compare with your peers?
Providing you the industry statistics to better evaluate and fine-tune your privacy program is the continuing purpose of this benchmarking article series, and our intent with the benchmarking figures we share from the RadarFirst platform. It has long been our mission to bring more clarity and light to incident response issues. We hope to arm our colleagues in the field with metrics and data so we can all know if we’re doing well — or if not, so we can identify areas to improve.
Benchmarking 101: How often do you notify regulators and individuals of a data breach?
One of the best places to start when establishing benchmarking metrics for your organization is your data breach notification rate or the number of incidents that are considered notifiable under the jurisdictional requirements.
Let’s first say: There is a presumption of breach whenever there is unauthorized disclosure, regardless of whether that incident was intentional and malicious or inadvertent and incidental. There is always a presumption that the incident is notifiable unless the organization can demonstrate that the incident has not reached the threshold for notification under the definitions of the applicable regulation. The burden of proof is always on the organization.
Now, in reality, with best practices in place, organizations with a strong culture of privacy are likely able to mitigate the risk of some or most of the unauthorized disclosures and prove that notification is not required. But the key is doing so based on a defensible and documented incident risk scoring process, demonstrating that consistent decision making is taking place.
Our metadata shows that, after having undergone a multifactor incident risk assessment and scoring the severity of the incident against the sensitivity of the data involved, only 6% of incidents in 2019 to date have required notification. Sufficient post-incident risk mitigation is beneficial to affected individuals and impacted organizations and is a critical contributor for lowering the overall notification rate to this figure.
Excellent record-keeping, paired with a consistent framework, ensures you have fully documented your burden of proof should an audit take place.
What now? Making the data work for your organization
So now we’ve presented you with a pretty compelling figure: With a consistent and defensible incident risk assessment process in place, your peers have arrived at a 6% notification rate across all of their incidents. Say they get 100 incidents a year. Up to 94 of these incidents could be sufficiently risk mitigated to avoid notification while reducing the risk of harm to those affected and damage to your brand. Powerful stuff.
But how do you take this stat and use it to empower your privacy program?
First, by showing where you stack up. Is your organization’s performance above or under this figure? How about comparing your organization to others within your industry? Below are two industry breakdowns for notification rate. We’ve found that these highly regulated industries have their own specific regulatory complexities, and it’s helpful to pull healthcare and finance into their own categories for comparison’s sake.
Once you see how you stack up generally or against your specific industry, you can decide the risk to your organization in standing apart from your industry peers on this data point.
- Are you reporting more frequently than this? Your organization may be at risk of over-reporting, which can result in brand and reputational damage and could even create risk of private right of action, as in California under the California Consumer Privacy Act.
- Are you reporting less frequently than this? Your risk assessment model may not be scoring the risk of harm to individuals using a consistent and defensible methodology, which can result in missed notifications, enforcements and fines from regulators and again brand and reputational damage.
Either way, it’s important to know what the general industry data is. Comparative benchmarking statistics help us identify the areas we need to focus our attention, as perpetually overworked and under-resourced privacy professionals.
And this means there is real monetary value to you and your privacy program budget in doing this work. Collecting the data, performing the analysis and then ultimately packaging that analysis in a way that is consumable for those in positions of power within the organization to make decisions and allocate resources can very literally pay off in the long run.
In short, benchmarking data is a guidepost to ensure we are transforming our incident response programs in a way that mitigates risk, increases program efficiency and ultimately protects our brands.
About the data used in this series: Information extracted from RadarFirst for purposes of statistical analysis is aggregated metadata that is not identifiable to any customer or data subject. The incident metadata available in the RadarFirst platform is representative of organizations that use automation best practices to help them perform a consistent and objective multifactor incident risk assessment using a methodology that incorporates incident-specific risk factors (sensitivity of the data involved and severity of the incident) to determine if the incident is a data breach requiring notification to individuals and/or regulatory bodies. RadarFirst ensures that the incident metadata we analyze is in compliance with the RadarFirst privacy statement, terms of use, and customer agreements.
 Approved
Approved































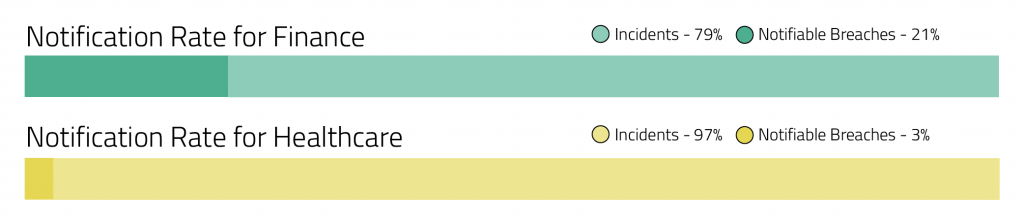
Comments
If you want to comment on this post, you need to login.